Protect your go applications and avoid antivirus false positives
Programs written in golang have no secrets.
Golang is a language that compiles to machine code, and many people think that the difficulty of decompiling its code should be at the C/C++ level, but in fact the difficulty of decompiling it is at the Java level
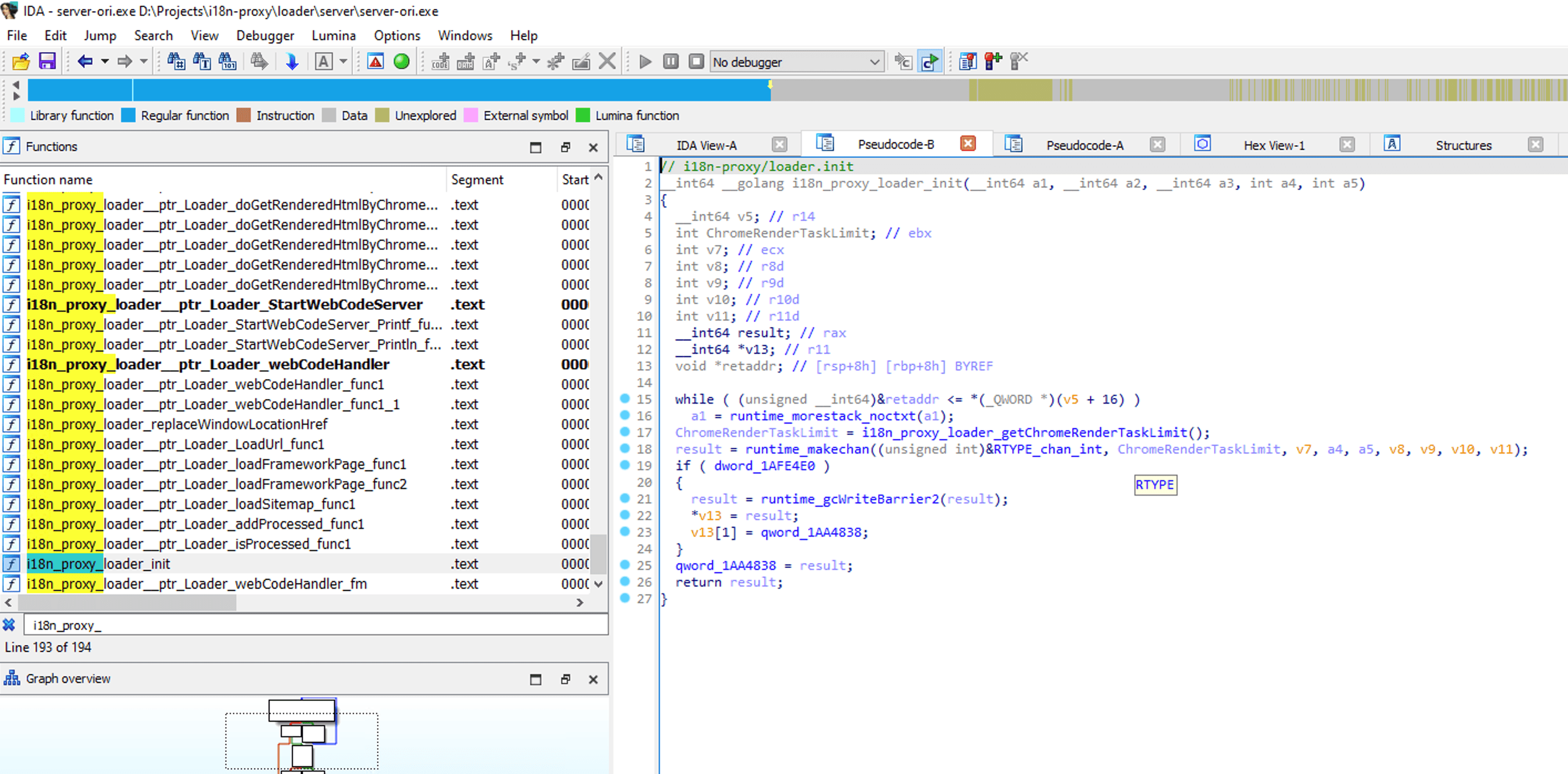
Here is an application written with golang, decompiled with IDA 8.3 Pro, we can see that IDA not only restores all the function names, but also restores the business code with good readability. And this program has used -ldflags "-s -w" to remove the debug information and symbol information when compiling, which shows that if no processing is done for the program written in golang, there will be no secrets at all.
Obfuscate with garble
Fortunately, we can use garble to obfuscate the code. The usage is as follows:
Download
go install mvdan.cc/garble@latest
Compile with obfuscation
garble -tiny build -ldflags "-s -w" [packages]
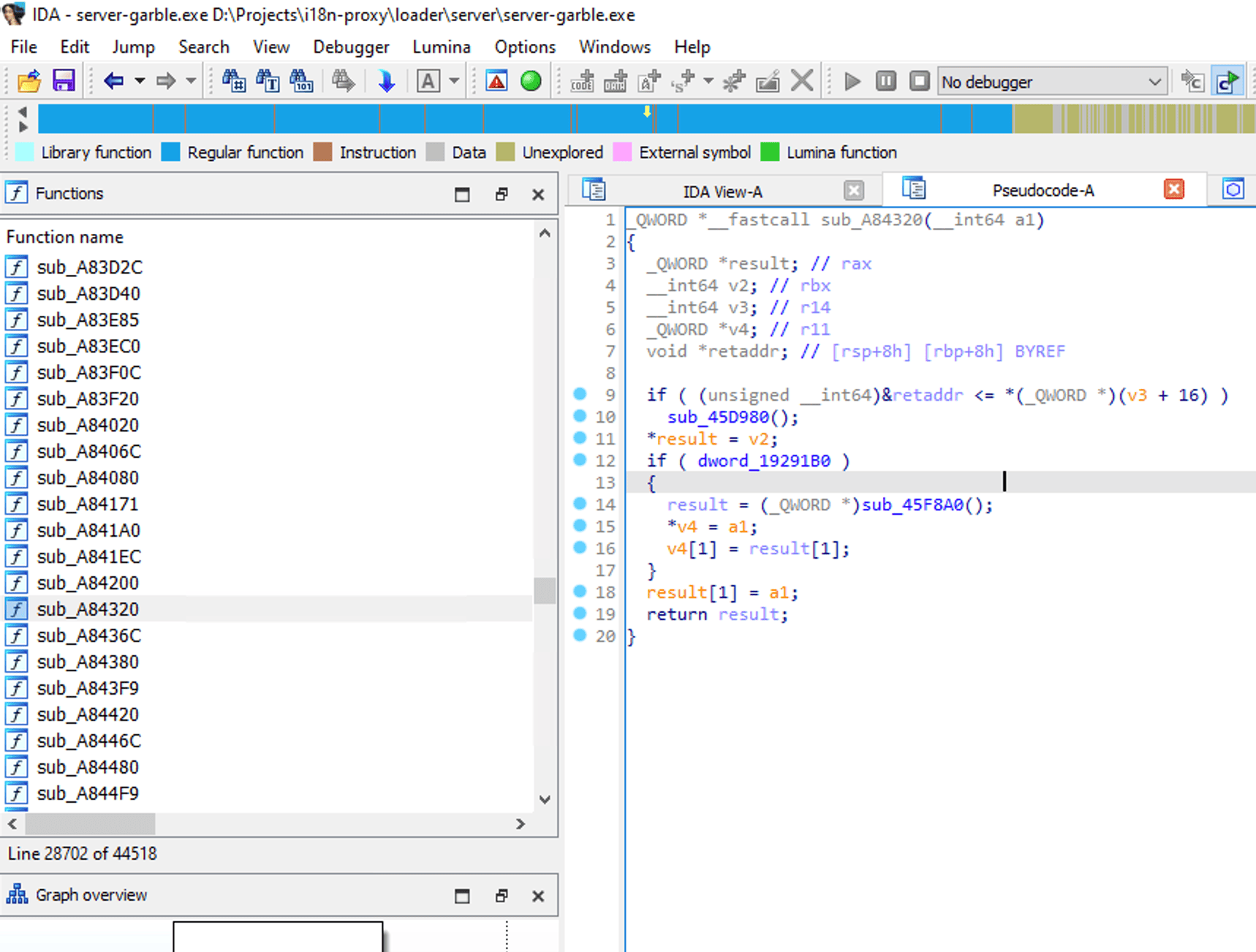
After compiling with garble, the compiled program is no longer naked like a normal golang program. When opened with IDA Pro, you can see that the program information has been hidden, and at least we can't get the program information as easily as before
The misunderstood golang programs
Although garble compilation solves the problem of code cracking and stealing, it also brings another problem, that is, most antivirus software will regard the program after garble compilation as a dangerous item, even if the program does not do anything malicious, many antivirus software still report it as a virus. The following is a simple hello world program, the code example is as follows:
package main
import (
"fmt"
)
func main() {
fmt.Println("Hello, World")
}
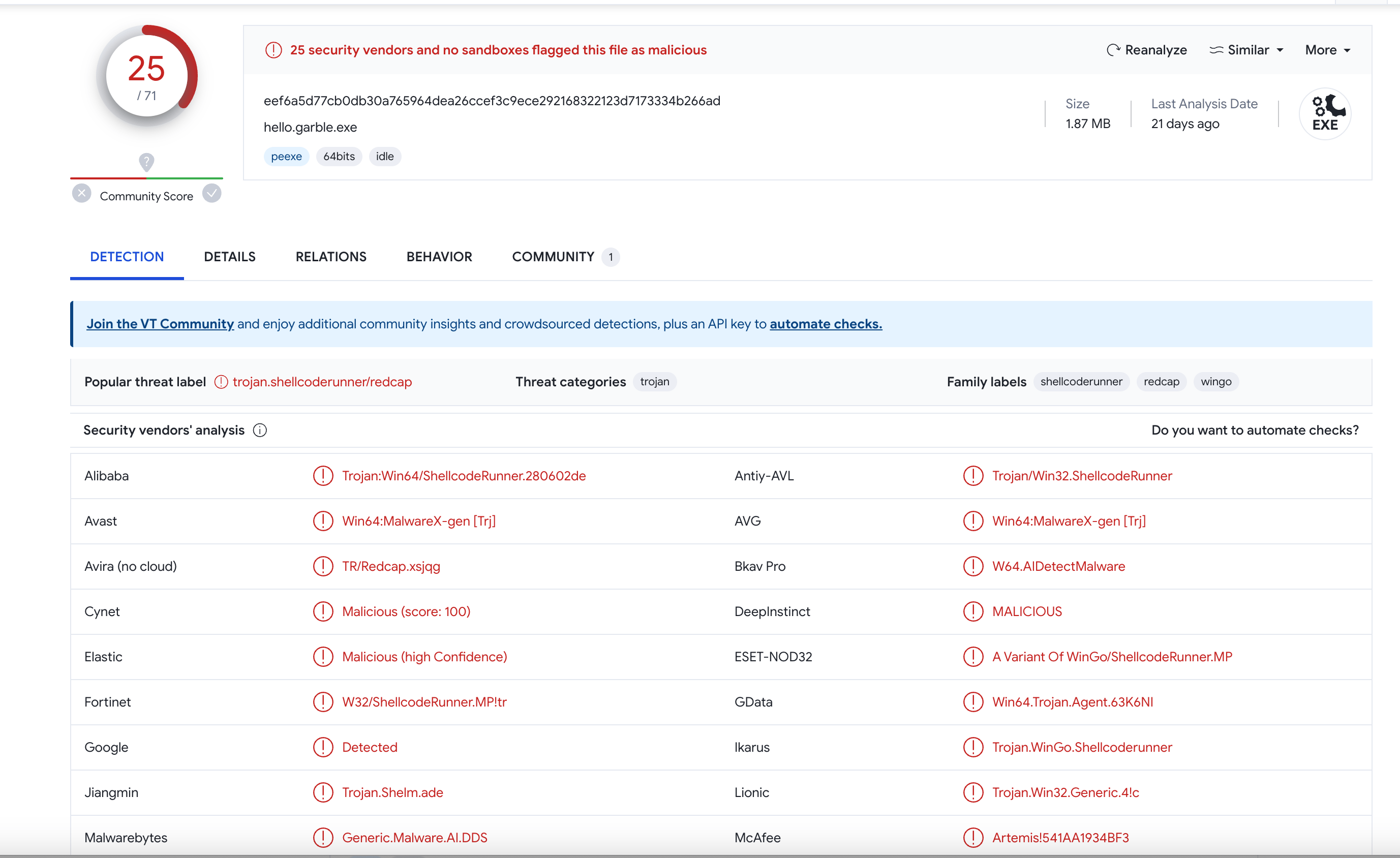
After compiling with garble, and submitting the program to VirusTotal, a large number of engines reported this program as a trojan or a virus.
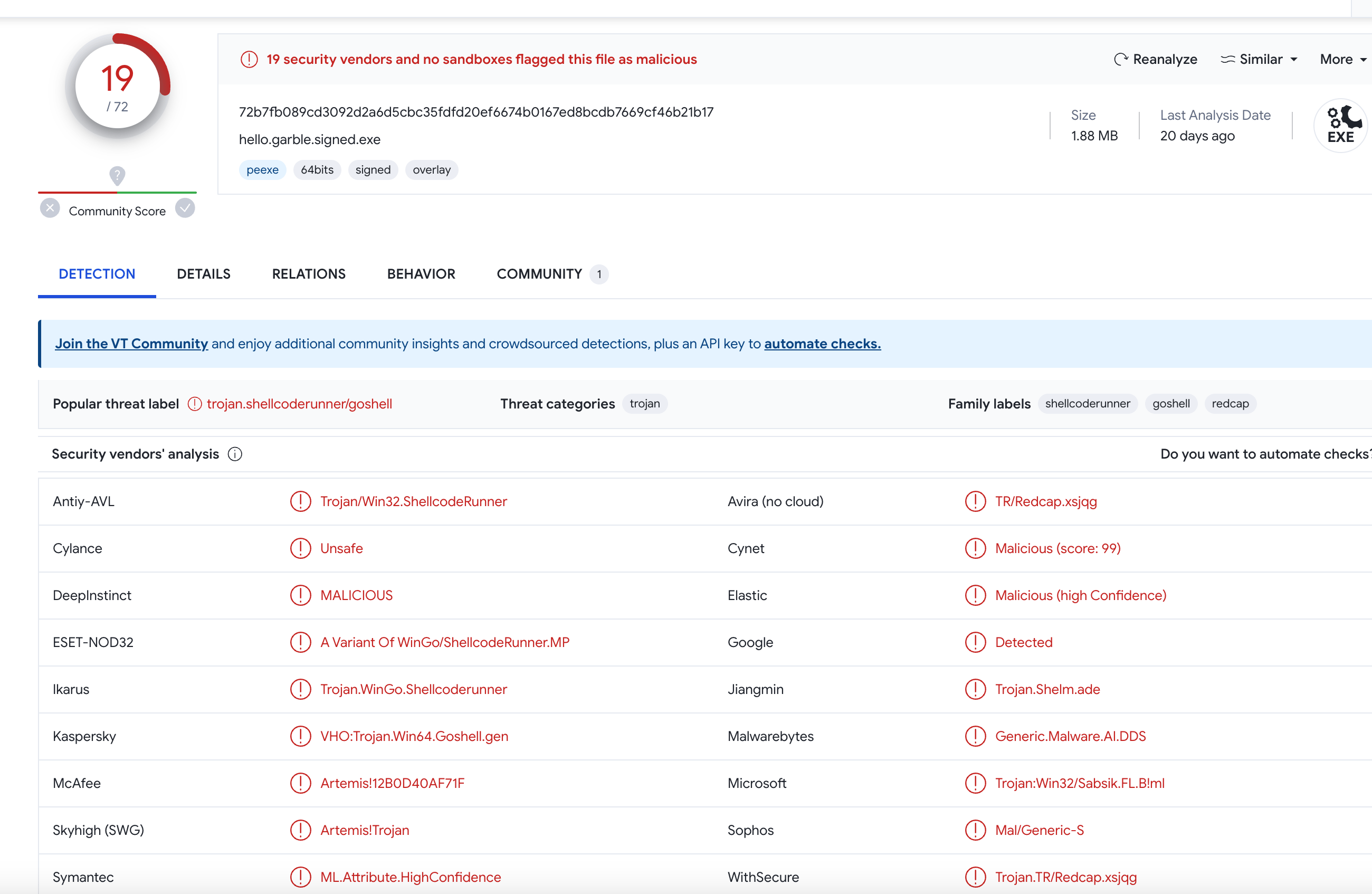
Even signed with an EV certificate, the number of false positives was only reduced by a sliver
As we can see, even though this program is devoid of any malicious behavior, for these antivirus engines, an obfuscated golang program is still recognized as a high-risk option.
Even if this program was not obfuscated by garble, compiled in the traditional way, it will still be flagged as malicious by many antivirus engines, regardless of whether it is signed or not.
This world must have misunderstood on Golang or Golang is used by too many people to write malicious programs, but this also damages legitimate Go programs
Packing golang programs
We developed a tool to provide packing service for Golang programs, preventing false positives from antivirus programs. After processing by our tool, 6 engines reported the program as malicious when without signing by digigal certificate.
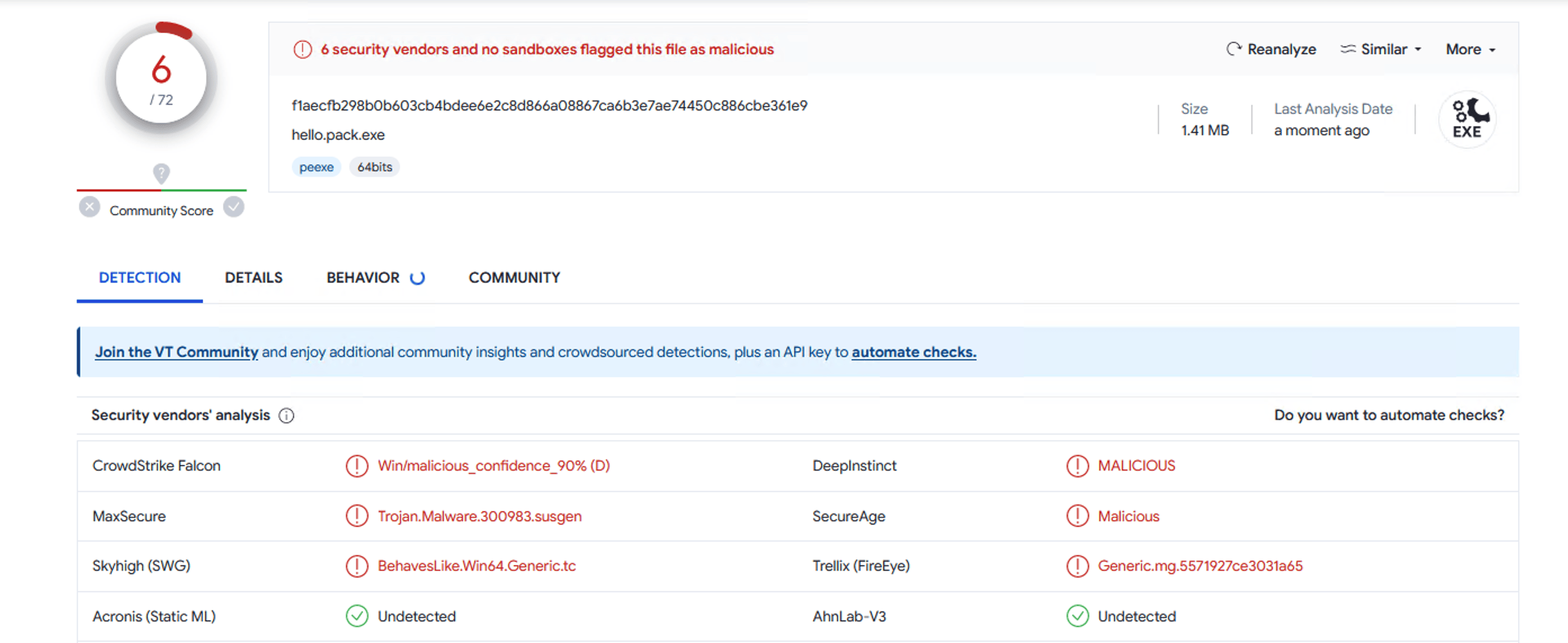
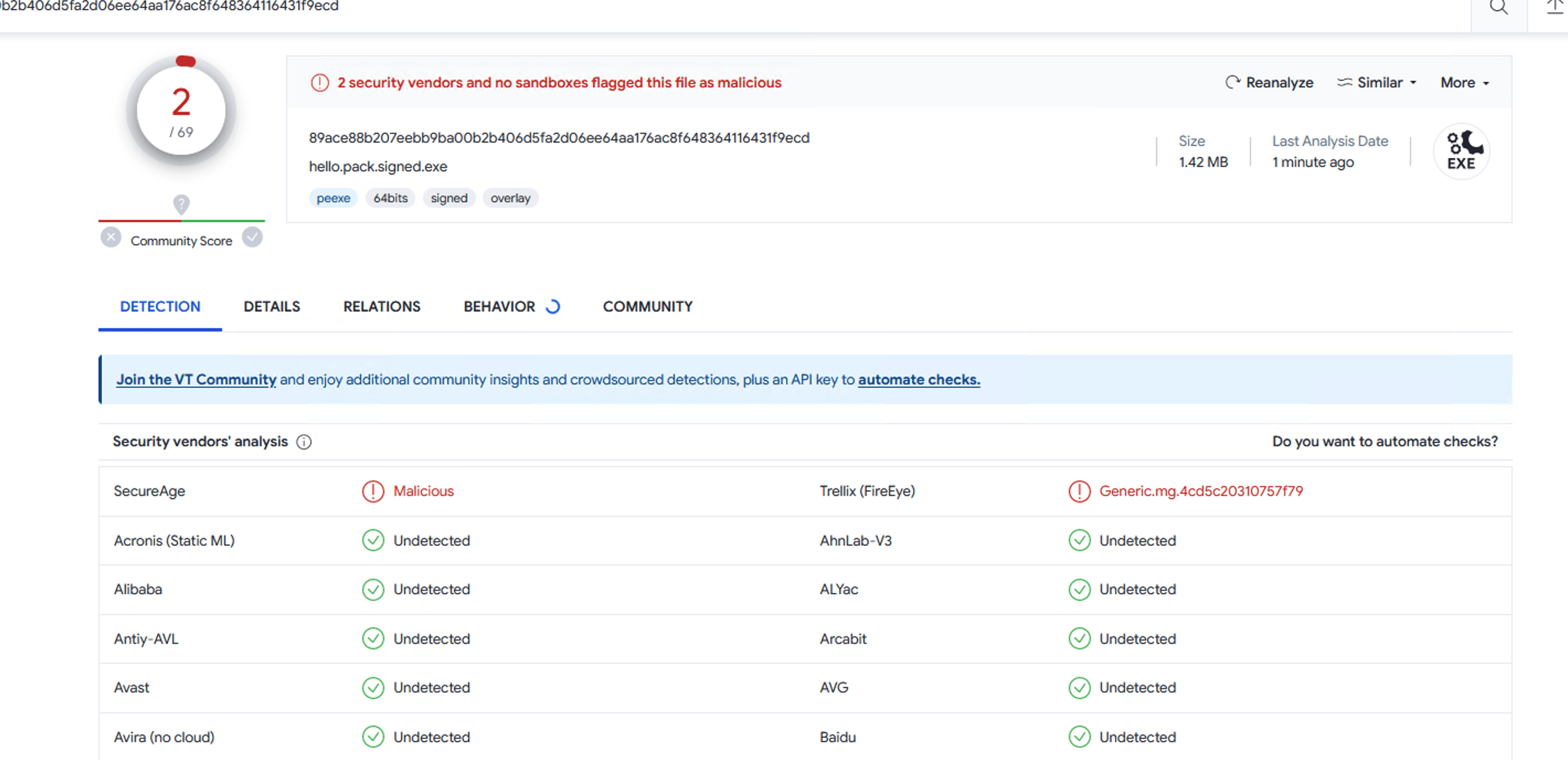
After signed with EV certificates, the number is 2, it can run normally on most systems at this situation.
How to use
1. Compile program with garble
garble -tiny -build -ldflags "-s -w" [package]
2. Download
Download gopacker from https://gopcker.dev
3. Pakcing the programs with gopacker
gopacker -i <exe-path> -o <output-path>
run with account information, need to purchase our product to get the license,the packed app is only valid for 7 days without license.
gopacker -i <exe-path> -o <output-path> --email <email> -p <password>
Notes
- It is recommended to use this tool together with a digital certificate, preferably an EV certificate.
- This tool is only for legitimate programs only. It is strictly forbidden to use it for any malicious programs.
- The data in this article is for reference only, and there may be some differences in VirusTotal data.